I'm a researcher and Ph.D. candidate at Security Lab at George Mason University, Fairfax, Virginia working with Damon McCoy. I am also a member of the Center for Evidence-based Security Research (CESR).
My interests are in the fields of Cyber-Physical Security. More specifically, my focuses are Cyber Threat Intelligence, Reverse Engineering (both Hardware and Software), Vulnerability Analysis and Ethical Hacking. The fundamental topics that I have worked on and influenced my research interests are System Security, Network Security, and Modern Cryptography.
Contact Details
Department of Computer Science,
George Mason University,
4400 University Drive MSN 4A5,
Fairfax, VA 22030 USA
GitHub
linkedin
Email: mrezaeir [at] gmu [dot] edu
pgp.mit.edu
Key Fingerprint:
BA91 5FB7 17B0 D855 4622
2108 15BD EAA0 46A2 0284
Publication
-
Schrödinger’s RAT: Profiling the Stakeholders in the Remote Access Trojan Ecosystem
Mohammad Rezaeirad, Brown Farinholt, Hitesh Dharmdasani, Paul Pearce, Kirill Levchenko, Damon McCoy
USENIX Security (Security 2018).
-
To Catch a Ratter: Monitoring the Behavior of Amateur DarkComet RAT Operators in the Wild
Brown Farinholt, Mohammad Rezaeirad, Paul Pearce, Hitesh Dharmdasani, Haikuo Yiny, Stevens Le Blond, Damon McCoy, Kirill Levchenko
IEEE Symposium on Security and Privacy (Oakland 2017).
-
A Security Analysis of an In-Vehicle Infotainment and App Platform
Sahar Mazloom, Mohammad Rezaeirad, Aaron Hunter, Damon McCoy
10th USENIX Workshop on Offensive Technologies (WOOT 16). [Slides]
-
A novel clustering paradigm for key pre-distribution: Toward a better security in homogenous WSNs
Mohammad Rezaeirad, Mahdi Orooji, Sahar Mazloom, Dmitri Perkins, Magdy Bayoumi
IEEE Consumer Communications and Networking Conference (CCNC 13).
Project
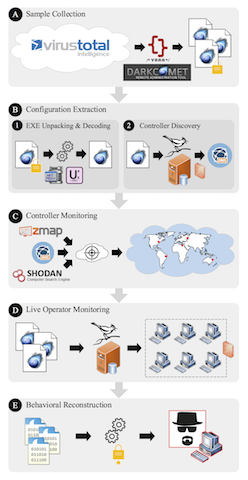
In this work, we design, implement and deploy improved methodologies for accurately measuring real victims that connect to our sinkhole, RAT-Hole and identifying RAT controllers using our scanner, RAT-Scan. The task of identifying victims at scale is made difficult by the number of pollution sinkholes receive from increasingly high-fidelity scanners and sandboxes. Differentiating between real controllers and sinkholes is also a nontrivial undertaking due to higher fidelity sinkholes. This increasing fidelity in RAT scanners that emulate more of a victim’s behavior and sinkholes that emulate more of a real RAT controller’s protocol has likely created an arms-race between entangled threat intelligence operations which we call Intelligence Pollution. This leads to inaccurate measurements and wasted notification efforts, wherein researchers and security vendors may confuse beneficent sinkholes for malicious controllers, or scanners and sandboxes for actual victims.
This project is aimed to shed light on DarkComet RAT operators from the behavioral perspective, and this includes operator life cycle and motivation when engaged with a victim machine.
In this work, we study the use of DarkComet, a famous commercial RAT. We collected 19,109 samples of DarkComet malware found in the wild, and in the course of two, several week-long experiments ran as many samples as possible in our honeypot environment. By monitoring a sample’s behavior in our system, we can reconstruct the sequence of operator actions, giving us a unique view into operator behavior. We report on the results of 2,747 interactive sessions captured in the course of the experiment. During these sessions operators frequently attempted to interact with victims via remote desktop, to capture video, audio, and keystrokes, and to exfiltrate files and credentials. To our knowledge, we are the first large-scale systematic study of RAT use.
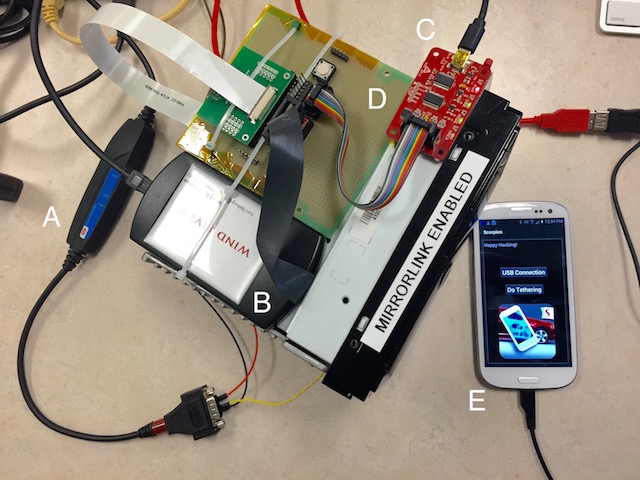
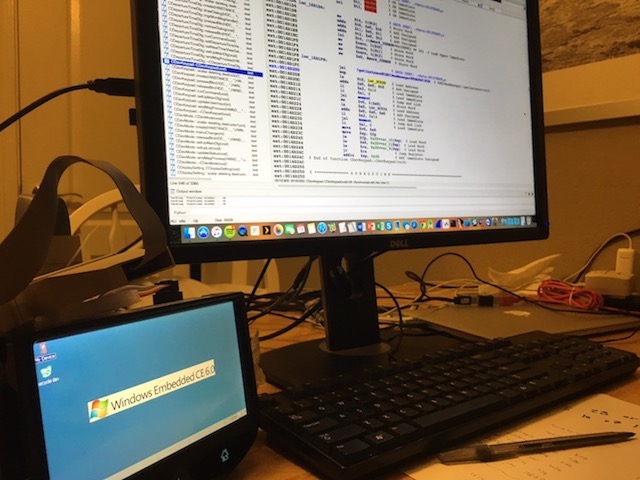
In this project, we performed a comprehensive security analysis on an IVI system that is included in at least one 2015 model vehicle from a major automotive manufacturer. We documented and demonstrated insecurities in the MirrorLink protocol and IVI implementation that could potentially enable an attacker with control of a driver’s smartphone to send malicious messages on the vehicle’s internal network. General Motors and DHS funded this work.