CRYPTON is selected to be a candidate for the future Advance Encryption Standard (AES) due to its high level of security, feasible implementation, and high performance. The algorithm was provided in software in both C and Java codes. In the project, a hardware implementation of the algorithm is considered. This specification provides the guidelines to implement CRYPTON in hardware, and outlines the performance of the algorithm in Field Programmable Gate Arrays (FPGA). Due to the space limitation of the device space, twelve-round scheme will not be used. Instead, the focus will be on two-round implementation. If time allows, the number of rounds in the implementation may be increased. The specification contains the following sections:
Section 1 discusses the overview of this documentation
Section 2 lists references and relevant documentation
Section 3 discusses the functions and the and the architecture of the design
Section 4 describes the design methodology to be used
Section 5 outlines the procedure for testing the functionality and performance of the design
Section 6 discusses the areas that may be changed depending on the project progress
Section 7 lists the schedule of tasks to carry the project
Lim, Chae. “Specification and Analysis of CRYPTON”, Version 1.0. December
1998.
The circuit consists three main functional blocks. These are Encryption/Decryption, Key Schedule, and Inbound Controller. The Encryption/Decryption block will perform both encryption and decryption. The scheme for both encryption and decryption will be identical, but the key scheduling is different in one process from the other. Key Schedule is an important process in the CRYPTON algorithm, and has to work in synchronization with both encryption and decryption. The Key Schedule will be responsible for scheduling the keys properly for each mode encryption or decryption. The Inbound Controller will provide synchronization between Key Schedule and Encryption/Decryption blocks. Figure 1 shows the block diagram of the CRYPTON design.
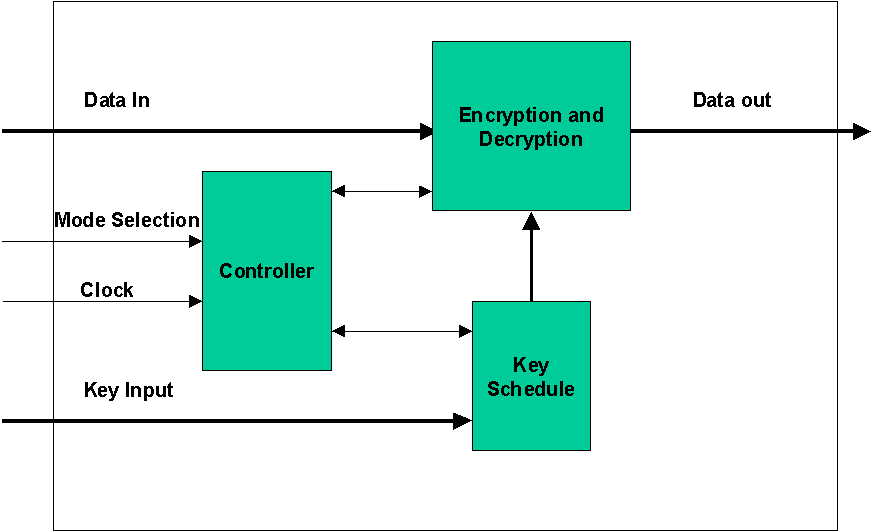
- Key Schedule
- Encryption/Decryption
- Controller
Key Schedule will take in 256-bit user key, and schedule the keys for
all rounds of encryption and decryption The key scheduling mechanisms for
encryption will be different from the decryption. The 256-bit user key
is fed to the Key Schedule block serially. This block will implement the
algorithm of key schedule as specified in reference (1). Detailed design
of this block will be provided later as an appendix in the final report.
The design will adhere to the encryption/decryption algorithm CRYPTON.
In the encryption mode, this block will accept a 128-bit block message
and produce a 128-bit block cipher text. In the decryption process, the
cipher-text is fed in as the input and the deciphered message is produced
on the output side. The encryption and decryption processes are identical
in this block, and the Key Schedule block will provide proper keys to carry
out the operation. Detailed design of the block is still to be defined.
The design will mainly use VHDL to implement to algorithm. Schematic capture option may be used at the top level to show main functions of the design. Xilinx will be the target of the implementation, but depending on the number of configuration logic blocks used (CLB), the specific device will be chosen. At this time, Xilinx XL4013E will be the candidate target of the implementation. Please note that the tool selection will be determined by the availability of the tools and our accessibility. Further information of the design methodology is listed in Table 1.
| Design Entry | Mainly VHDL; schematic may be used at top level; Logic Blox may be used |
| CAD Tools | Synario and/or Xilinx Foundation Series |
| Simulation | Aldec Evaluation version 3.3 or Model Tech |
| Device | XC4013E, or maybe a bigger device |
| Synthesizer | Metamor, or Cadence |