Anonymous Remailers
Overview
An
anonymous remailer is specialized kind of mail server designed to send e-mail
messages without identifying the sender. Many of them are provided as a free
service.
Imagine
being in protective custody or being a journalist and you want to get an e-mail
out without being discovered. You decide to use an anonymous remailer to remedy
that issue. These systems strip all headers from the message making it next
to impossible to trace where the message originated. Some systems gave you an
anonymous address that other people can send mail to, which will be forwarded
on to your regular e-mail account. This is sometimes known as a “pseudonymous
server”. However, the majority of remailers use encryption. In addition to remailer
technology, ther eare a variety of attacks that remailers face.
Types of Remailers
Pseudo-Anonymous Remailers
With a pseudo-anonymous remailer, the operator of the remailer
knows the user’s true e-mail ID. The user’s messages are sent with an untraceable
(and “anonymised”) return address. These remailers are easy to use, but you
are anonymous only because the operator promises to keep your identity secret.
While these remailers are committed to protecting your identity, courts occasionally
force these remailer-operators to reveal particular clients (based on crimes
ranging from harassment to child pornography).
Pseudo-anonymous remailers are probably sufficient for most
people’s needs (e.g., posting comments or sending a resume).
Anonymous Remailers
True anonymous remailers provide a much higher guarantee of
privacy and anonymity. They are essentially computers designed as specialized
e-mail servers. While traditional e-mail servers track and preserve all incoming
and outgoing sender, receiver, and message information, anonymous remailer servers
are designed to strip out all identifying and traceable information. While there
are a number of steps involved, truly anonymous remailers use encryption to
disguise the origin of messages. There two basic types.
Cypherpunk remailers were a big advance over the pseudo-type
of remailers. They provide anonymity without even using an anonymized return
address, in large part through encryption
Mixmaster remailers are the latest generation of anonymous
remailers. It requires a special message format and a specific software package.
This type of remailer uses advanced techniques and strong cryptography to make
most methods of traffic analysis next to impossible.
The structure of current remailer messages is a nested set
or encrypted messages. The message contains the instructions for each remailer
and the message to be forwarded. Each remailer removes a layer of encryption,
accompanying instructions, takes any requested actions, and sends the message
on. An example of this is Figure 1 (shown below).
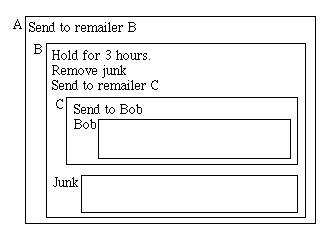
This figure shows a remailer that gets sent through three remailers
(A,B,C) and finally to Bob. The boxes represent encryption, with the name of
the person to whom the message is encrypted, outside the upper left corner of
the box. One thing to note is that the message shrinks after each hop.
Mixmaster remailers are also known as cyberphunk remailers.
These do several things:
·
They send a
message to another e-mail address or post it to a news group.
·
They accept
encrypted messages with instructions for processing hidden inside the encrypted
envelope.
·
They strip all
mail headers.
·
They add new
headers such as subject lines.
·
They remove
some information from the end of the message.
·
They encrypt
part of a message using a key specified in the message.
Attacks
Attacks are actions taken against a remailer when a message
is trying to be sent. I will explain six very serious attacks that happen to
remailers when they are not careful.
Threat
Model
An attacker is able to record the contents of all messages
into and out of all remailers, along with the times they arrive and depart.
All messages are monitored as they leave the sender’s machine and as they arrive
at the destination.
The attacker is also able to send an unlimited number of messages
through the remailers, including previously intercepted messages. The attacked
can also prevent messages from arriving at their destinations.
Trivial
Attacks
This can happen to anyone when the message that is sent is
unencrypted. This can also happen when the message is encrypted, only if the
remailer is compromised because the operator knows both the originating and
final addresses.
Reordering
Messages can be traced through chains of remailers with encryption
because incoming messages are forwarded directly after processing. When a message
arrives, another one leaves immediately. The attacker knows that these are the
same messages despite all precautions and can even be known by using mail logs.
The first fix to this problem was to delay incoming messages
for some random length of time before sending it out. However it depends on
the traffic. If there are many messages arriving in the average holding time,
then the identity of the message is reasonably well disguised. If there is very
little traffic, due to network outages, etc., there is little or no protection.
Reordering always involves keeping some number of messages
in the remailer at all times. These messages are called the message “pool”.
The most efficient way to do this is to have N messages in the pool and send
out one of the (N+1) messages in the pool, which is chosen at random. Unfortunately,
this scheme is susceptible to “spam” attacks.
To keep that from happening, another idea was proposed. It
was decided that instead of sending out one message, all messages should be
sent out at once periodically and at a random time.
Size
and Distinguishability
Your message can also be tracked by size. Default messages
automatically decrease in size by a small amount at each hop. Padding is removed
from each message by the remailer, at each hop however, this is only to decrease
the size of the message. Extremely large messages also stand out and will also
be decreased yet will remain bigger than other messages. Because each comes
in different sizes, attackers can pinpoint a message and “attack” it.
The solution that was found to be that each message should
be the same size.
Replay Attack
This type of attack can be used to follow a message to its
final destination or backtrack from the end to its original sender. To trace
a message forward, the attacker captures your message and sends many copies
to the first remailer. Many identical messages will then emerge from the remailer
and move on to the next remailer. This bump in the remailer traffic will show
the route of the message.
To prevent this attack, remailers must refuse to send a message
more than once. This can be done by including a random ID number for each hop,
which the remailer records. This also has the benefit of making spams expensive.
Man-in-the-Middle Attack
This attack deals with the initial public key exchange by intercepting
the very first message to a new correspondent and substituting a genuine public
key with a fake one. In order to exchange messages, you need the other person’s
public key and they need yours. Once you get it, you put it on your Public Key
Ring. It is the very first message with the public key that is vulnerable. If
precautions are taken, there is no more threat.
This attack is not limited to the Internet either. This could
have been done a thousand years ago with plain old postal mail (snailmail).
For example, suppose to merchants in England and Germany, who never met in person,
wanted to communicate over mail. The Englishman approaches the German with a
business proposal and he signs his letter. How could the German know the signature
is authentic? A crooked postal clerk in France could intercept the message,
rewrite it himself, pretending to be the Englishman. If the German admits the
signature the French postal clerk would intercept all future correspondence,
replace it with rewritten letters and contracts, and keep pretending to be the
Englishman.
In the digital age, an attacker can get access to one of the
Internet nodes through which your message hops. Then:
1.
Malice intercepts
your message.
2.
They will remove
your public key and save it for themselves.
3.
They generate
their own private + public key pair.|
4.
They attach
this newly generated public key to your message, instead of the original.
5.
You send the
tampered message to IDS.
If IDS accepts this bogus key, the following would happen:
1.
IDS writes a
confidential message to you.
2.
IDS uses the
bogus public key to encrypt the message.
3.
IDS sends the
encrypted message via e-mail.
4.
Malice intercepts
the message.
5.
Malice deciphers
it using the private key they created.
To prevent the attack from happening, you should use a digital
signature certificate from a qualified company, exchange public keys in person
and on disk, and/or download public keys over a secure website.
How
a Remailed Message is Constructed
After going on to sendfakemail.com, you can go to an access
page that will generate a list of remailers at random for you. This list shows
their “screenname”, the configuration options, and special features. It also
shows its twelve-day history, average latency, and uptime for each remailer.
An example of the first part is below:
$remailer{"anonmtq"}
= " cpunk mix hybrid pgp latent ek ekx esub cut hash post repgp remix reord
ext max test inflt75 rhop5 klen500";
To decipher this:
·
“anonmtq” is the screen name
·
cpunk – a major class of remailers,
supports-request remailing
·
mix – can accept messages in
Mixmaster format
·
pgp – remailer supports encryption
with PGP – a short name instead of the full e-mail address will be shown.
·
Latent – is a late time option
·
Ek – encrypt responses in reply
blocks using encrypt-key: header
These are just a few of the many configuration options used.
It is almost like deciphering a code. An example of the second part:
noisebox remailer@noisebox.remailer.org ++++++*++++* 19:15
99.99%
·
The first part
is the fake e-mail address used.
·
The second part
is the response time over a 12-day period.
·
(The + stands
for less than four hours and the * stands for less than one hour.)
·
The time is
the “uptime” that is has been in use.
·
The percentage
is the average latency.
Related Links
Anonymous Remailer FAQs
White Paper – Anonymous
Remailers
Anonymous Remailer Information – Electronic
Frontiers Georgia
Anonymous Remailer Information
– Riot Anonymous Remailer
Anonymous Remailers,
General Information on the Concept of Anonymity on the Web
New
Order Anonymity/Privacy Tools
Andre Bacard’s Privacy Page
Anonymizer Privacy Products
Free Anonymous Remailers You
Can Use
The Offshore MixMaster Anonymous
Remailer
Riot Anonymous Remailer
W3 Anonymous Remailer
a joint project of the George Mason
Society and the Global Internet Liberty Campaign
